Filesystem/Volume encryption has become paramount to the masses in the IT industry due to the varying advantages it presents including protection of sensitive data, military-grade encryption standards, password keys to prevent unwanted access, and an encrypted file/drive only the encryption software can access among others.
Veracrypt is a cross-platform and open-sources on-the-fly encryption tool that was originally based on Truecrypt’s 7.1a codebase back in June 2013 but has since then matured greatly to become a singular encryption solution that is now dissimilar and incompatible with volumes encrypted with Truecrypt.
Veracrypt is essentially your go-to option for an encryption tool if you’re looking to replace Truecrypt.
Installing Veracrypt in Linux
The installation of Veracrypt is pretty easy and downright straightforward. Before anything, you’ll need to download the Veracrypt Generic Installer package for Linux systems, after which you’ll extract it and run “veracrypt-1.xx-setup-gui-x64” as a program from the extracted folder as seen in the image below.
$ tar -xf veracrypt-*.tar.bz2 $ ./veracrypt-1.24-Update7-setup-gui-x64 [for 64-bit] $ ./veracrypt-1.24-Update7-setup-gui-x86 [for 32-bit]
On executing the installer, you’re prompted with the Veracrypt installer.
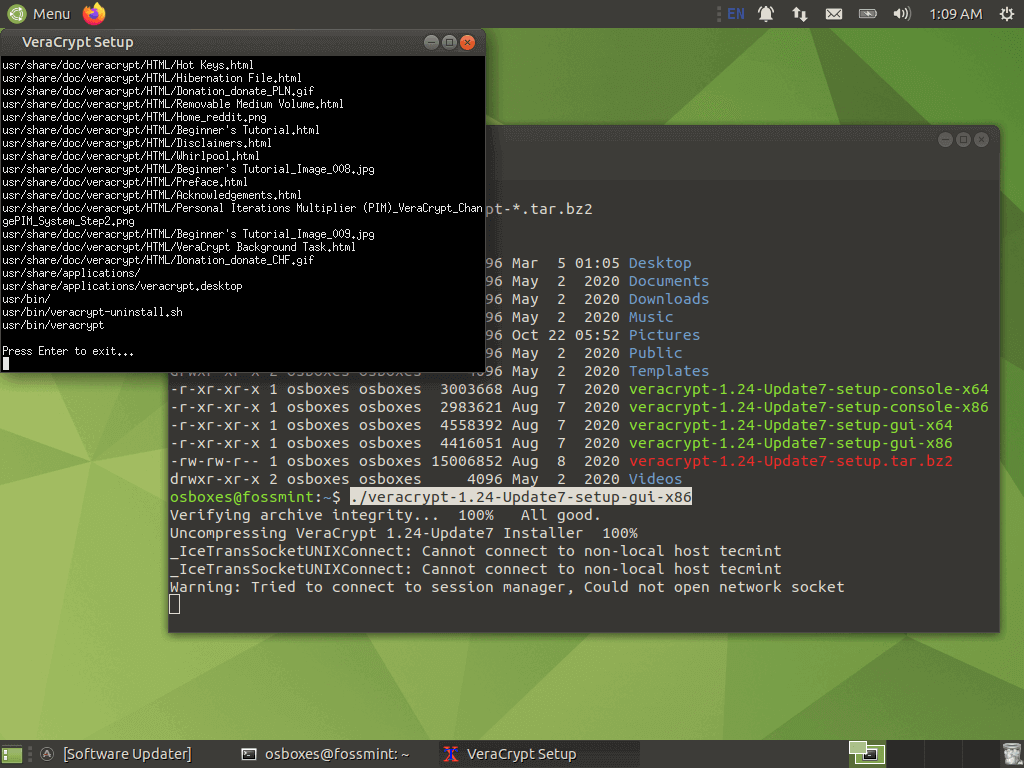
At this point, the installation is complete. You’ll press the enter key to exit the Veracrypt setup. The next prompt you’ll see immediately afterward is the uninstall dialog that basically gives you uninstall instructions. Should you be displeased with Veracrypt in the future, you can easily remove it by entering “veracrypt-uninstall.sh” in the terminal.
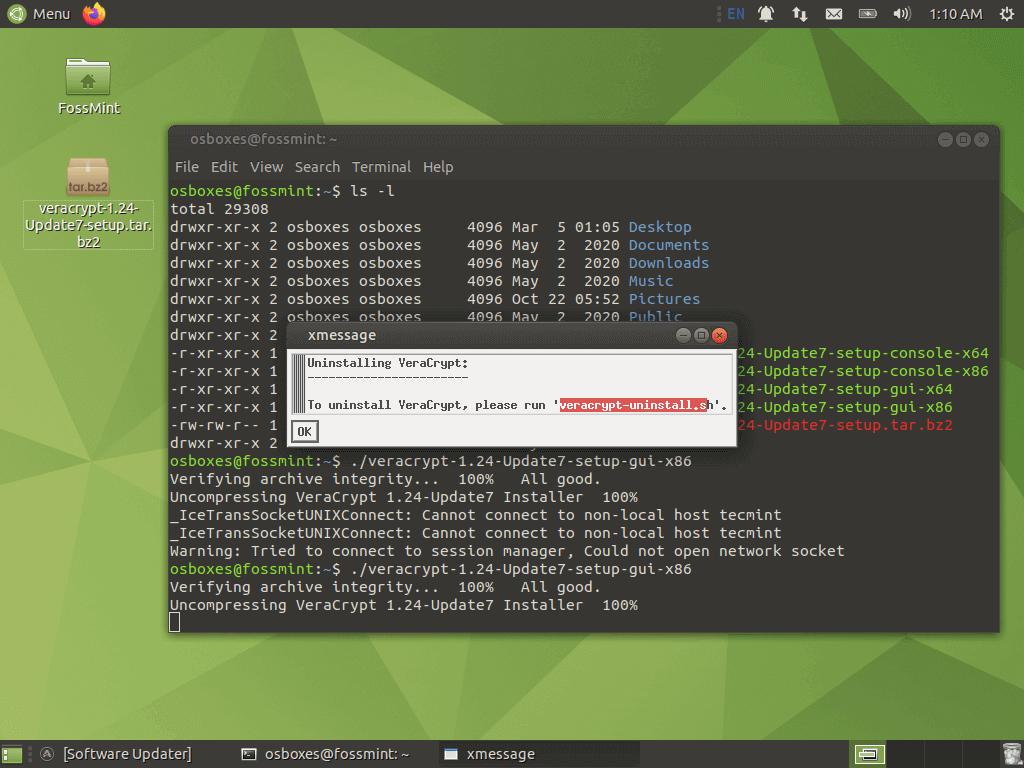
Creating Virtual Encrypted Disk in Linux
Start the Veracrypt from the Application Menu and click on the “Create Volume” button to create a virtual encrypted disk.
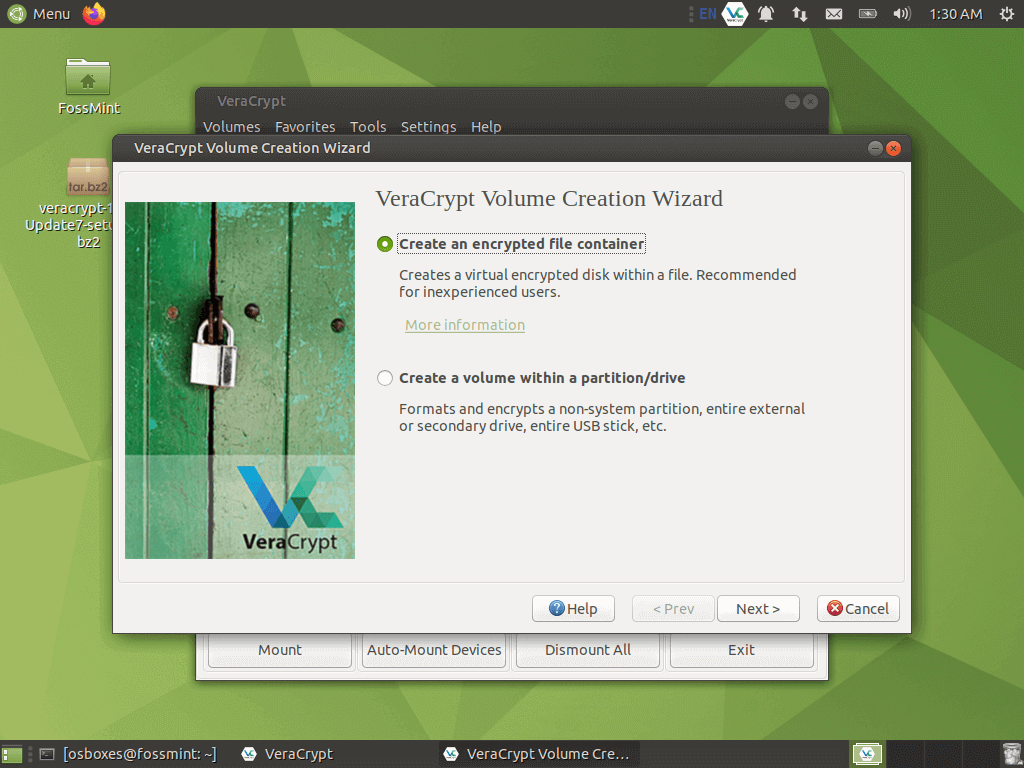
Select the Volume type.
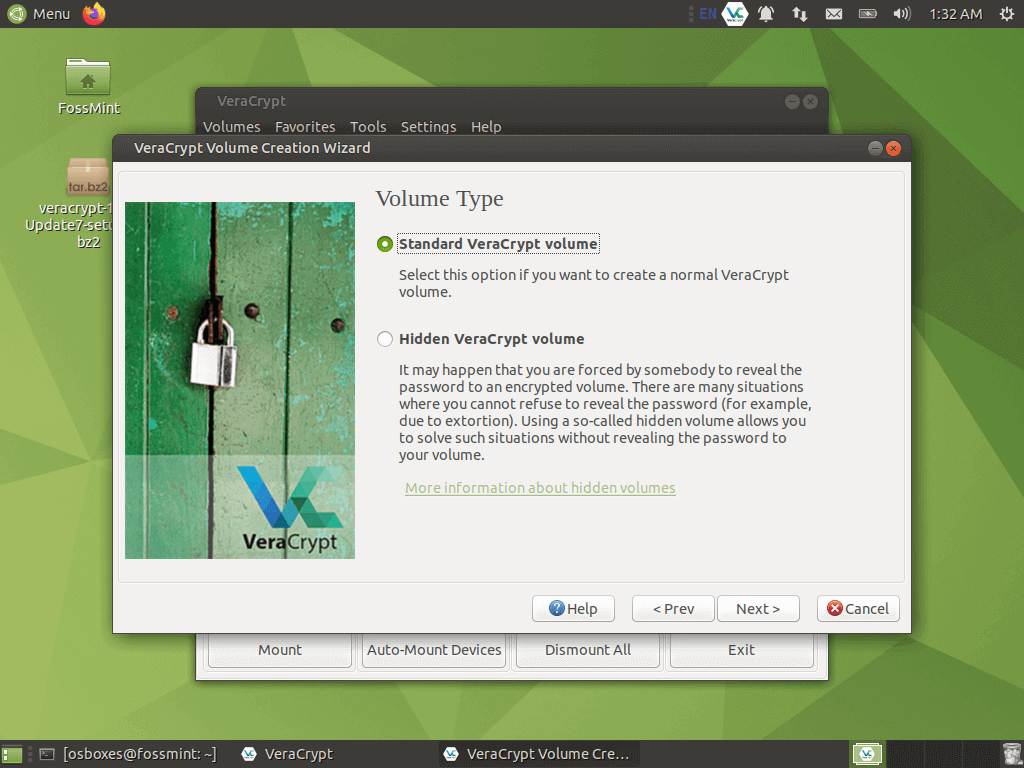
Choose the location of the directory at which you want to save your virtual drive.
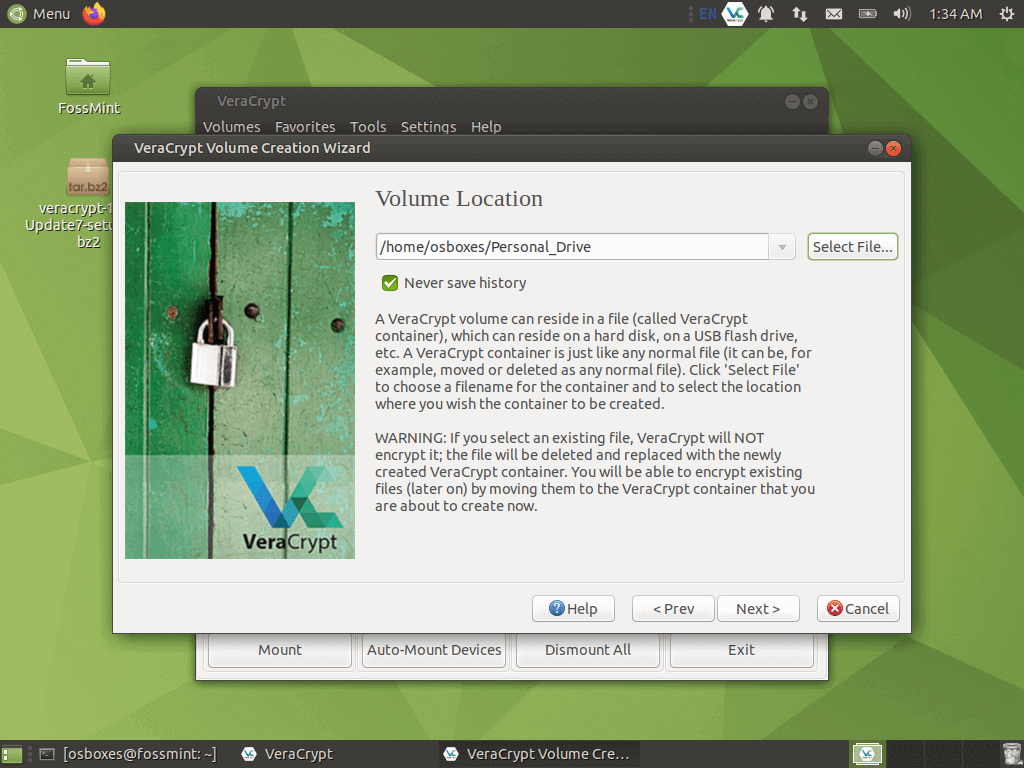
Allocate disk space to your drive.
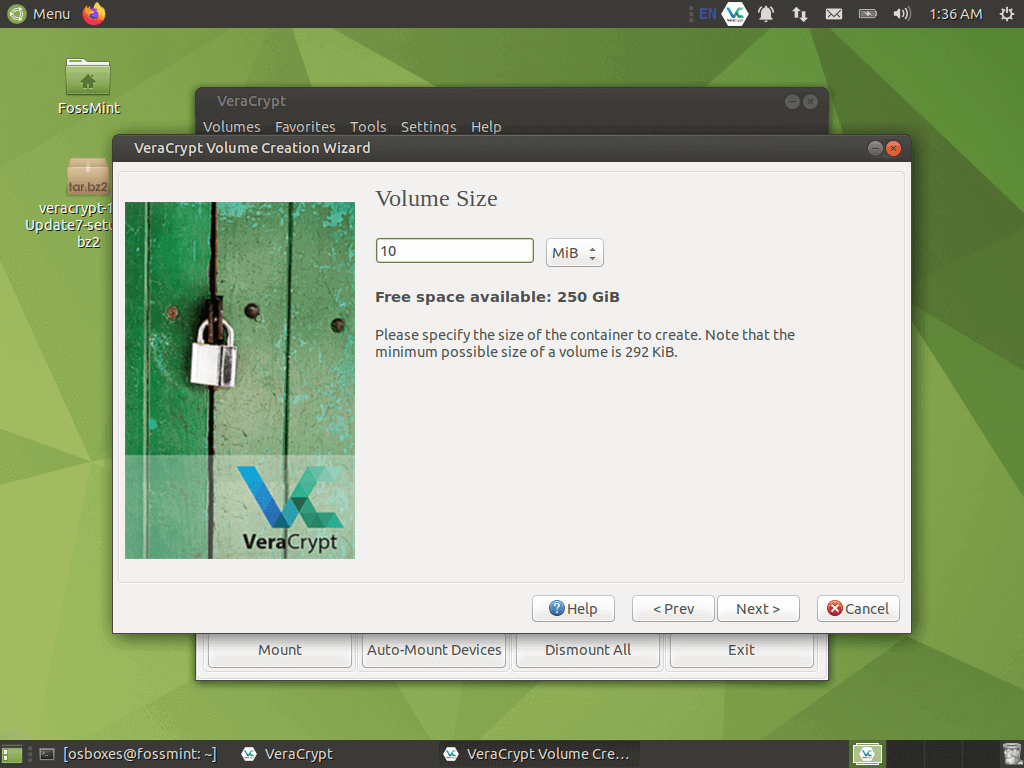
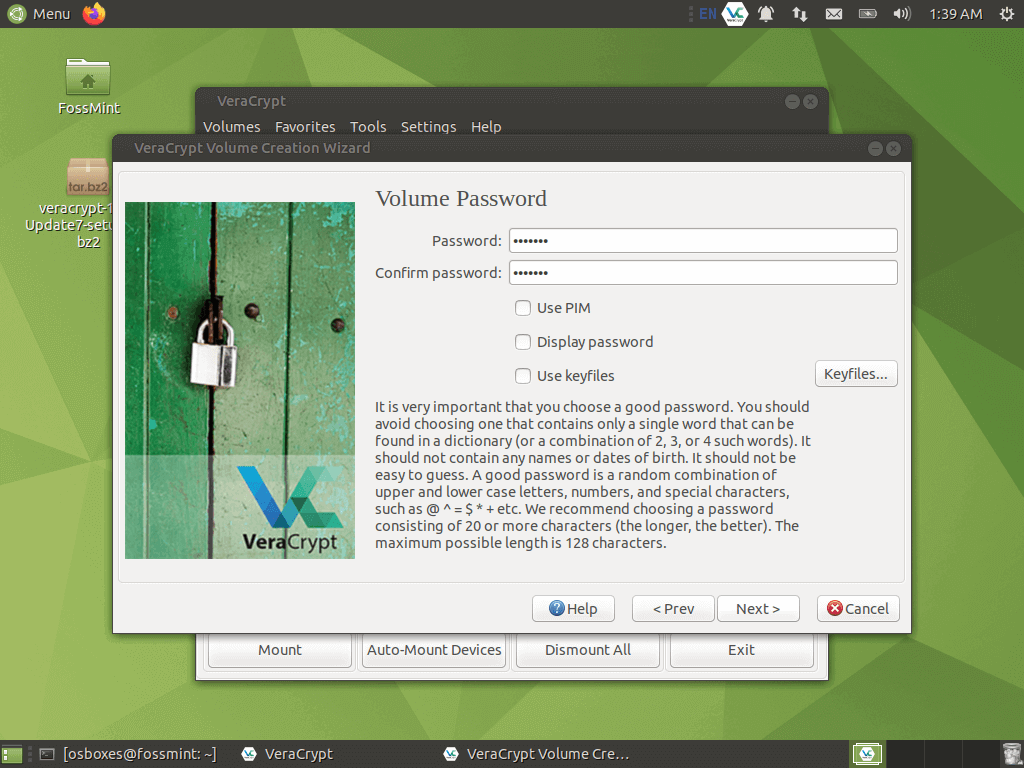
Create a password for your virtual drive.
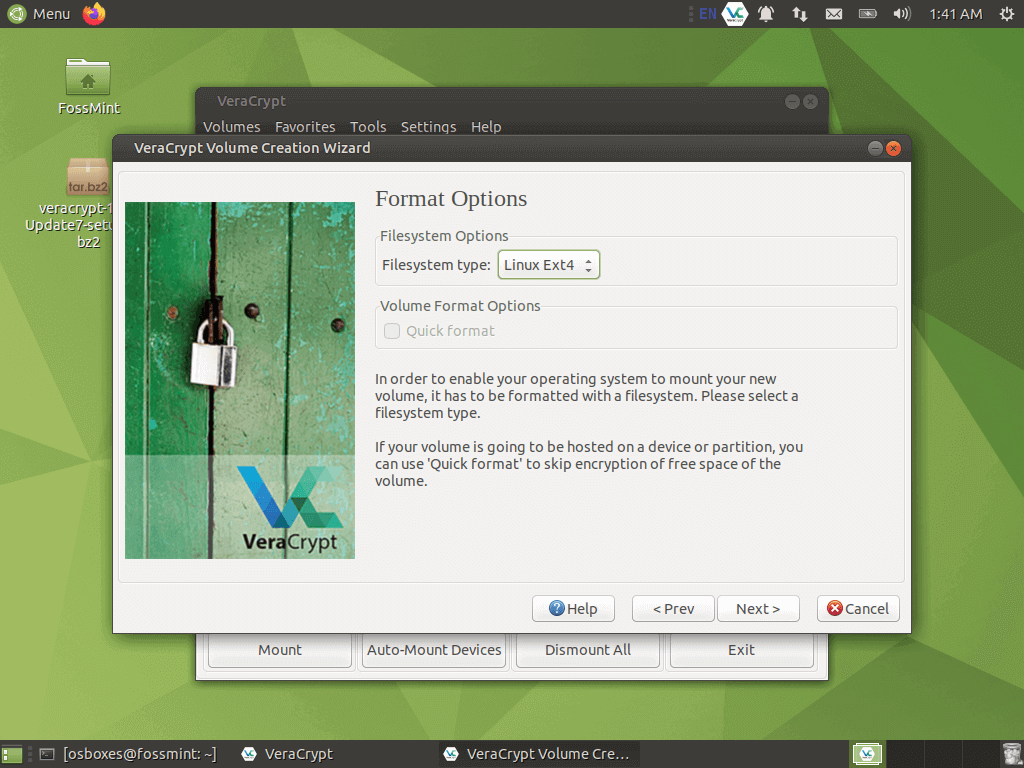
Choose the filesystem for your drive.
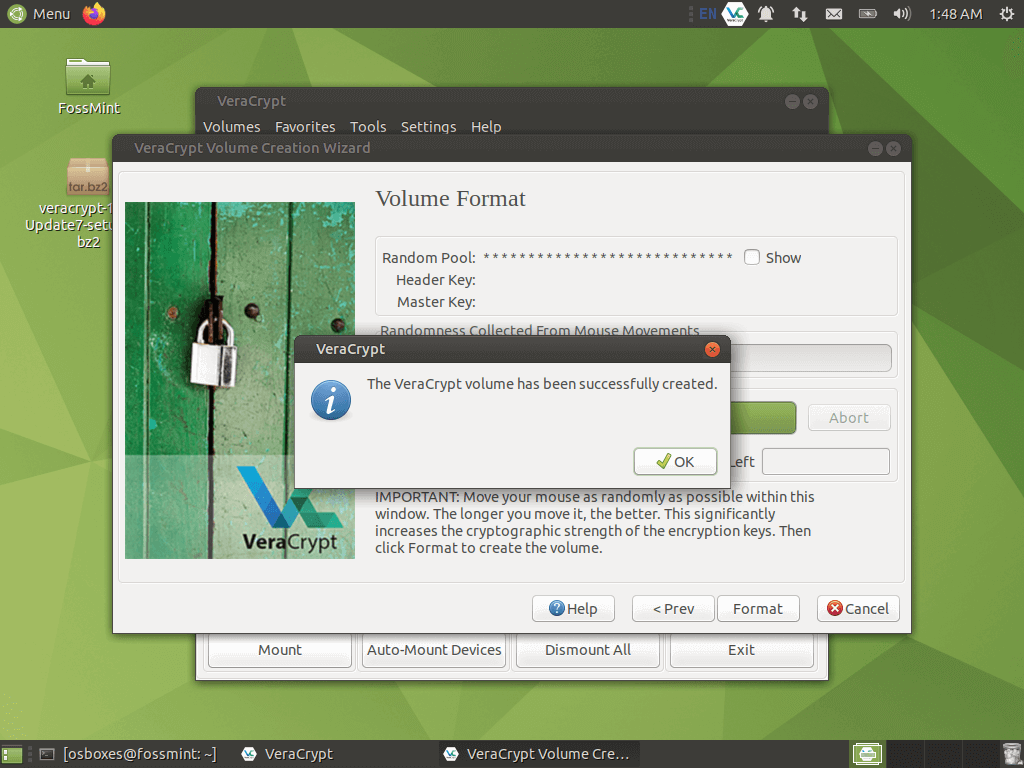
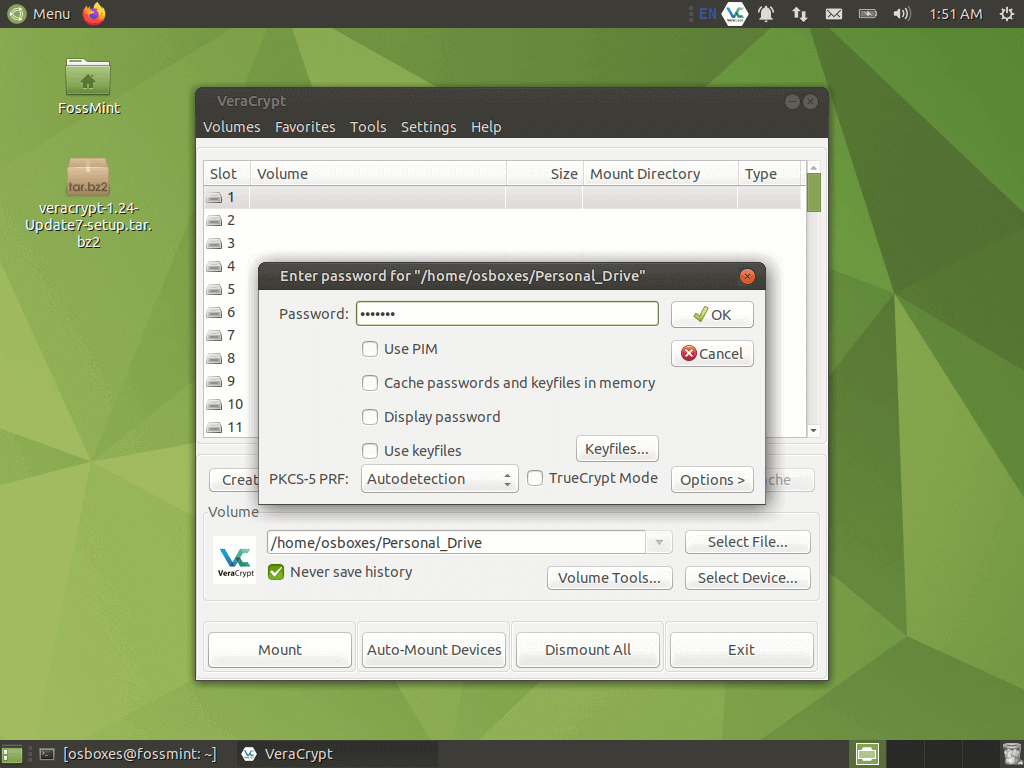
Once you’ve set your encrypted volume up, there’s nothing more to do than mount it in Veracrypt whenever you need to.
Do we hope you’ve found the installation instruction easy and straightforward? Should you run into any sort of problems, let us know in the comments below and we’ll reach back to you as soon as I can.

Comrade! What do you need such strong encryption for? I do not mean to pry, but I couldn’t help but notice you have also install the Tor Browser. It is not my business, I know, but it would be a shame if you fell victim to pornography or illicit drugs. Laws against these things are here to protect the interests of the prolitariat, comrade. I won’t mention this to anyone, but please, we need your mind focused on the revolutionary struggle and not degeneracy.
Tomb is also a cool command-line tool. It takes tools that are already installed/available and is basically a user-friendly wrapper for them. It also supports steganography- hiding your gpg key in a jpg.
https://www.dyne.org/software/tomb/