Over the years, I have come across many blogs that claim Linux is impenetrable by security attackers too many times to count. While it is true that GNU/Linux operating systems for desktops and servers come with a lot of security checks in place to mitigate attacks, protection is not “enabled by default”.
This is because your cybersecurity ultimately depends on the tools you have employed to sniff out vulnerabilities, viruses, and malware, and to prevent malicious attacks.
In today’s article, we turn our attention to system administrators and security enthusiasts who need to ensure the confidentiality of the data on network servers and local setups. What’s even cooler about these apps is that they are open-source and 100% free!
So without further ado, here is a list of tools that you must have installed on your machine as a security expert or enthusiast.
1. ClamAV – Linux Antivirus Engine
ClamAV is a robust free and open-source anti-malware engine built to scan for malware and viruses on Linux operating systems. It features multi-threaded scanning for detecting security attacks in real time by using their signatures for reliable identification.
While ClamAV ordinarily requires you to be conversant with the command line which might be a turn-off to first-time security enthusiasts, it comes bundled with the basic features one needs for malware and virus scans.

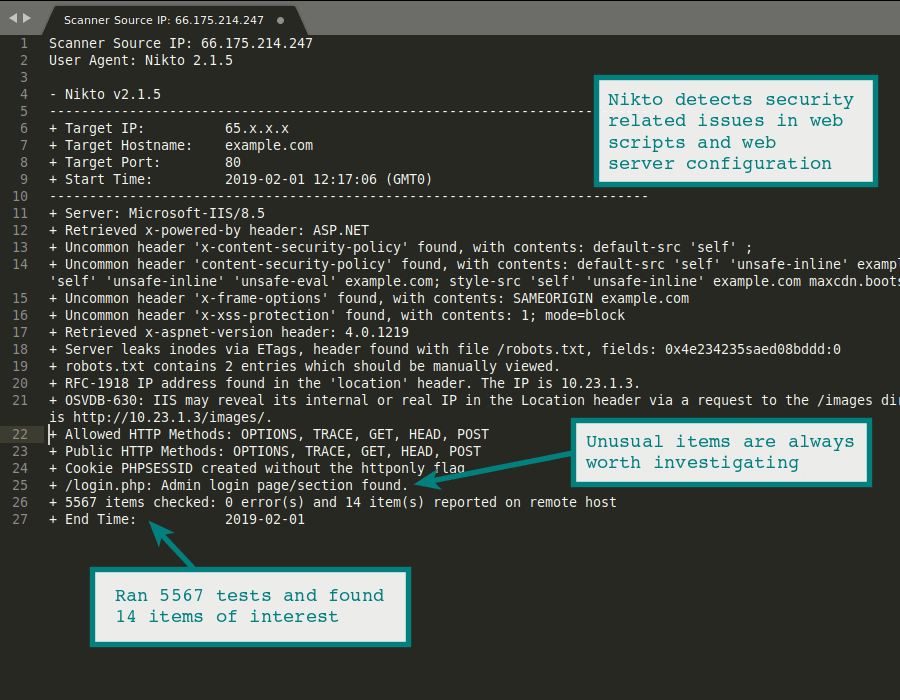
2. Nikto – Linux Web Server Scanner
Nikto is a web server scanner for performing comprehensive tests against web servers. The tests include checking for outdated server versions, checking for version-specific problems, auto-pause at a specified time, host authentication with Basic and NTLM, Mutation techniques to “fish” for content on web servers, presence of multiple index files, etc.
Nikto is free and open-source. Documentation is available on the site for Nikto2.
3. Nmap – Linux Network Scanner
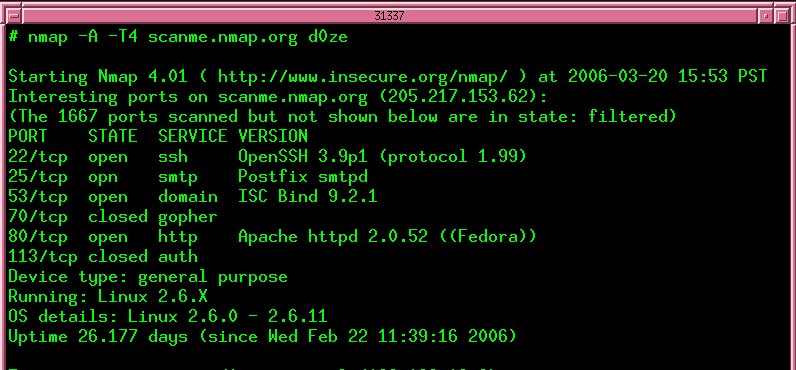
Nmap is a powerful free and open-source tool for scanning vulnerabilities in a network. With it, network admins can examine active devices in detail as well as discover available hosts, detect security issues in resident systems, and identify open ports.
Because Nmap comes with Several experts and even organizations rely on it to monitor multiple complex networks with tons of devices and/or subnets and single hosts.
With the ability to analyze IP packets and provide technical information on network devices, you can trust Nmap to come in handy every working day.
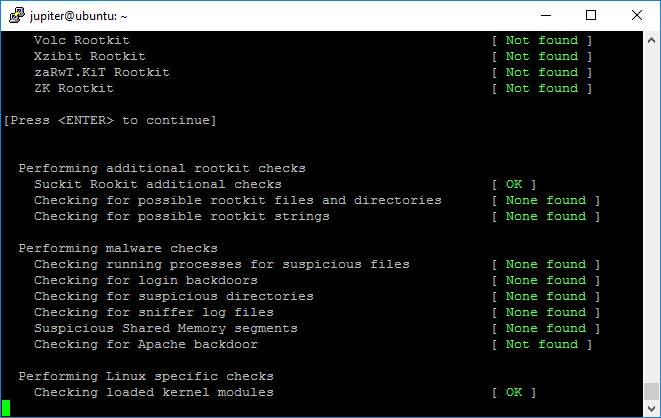
4. Rkhunter – Linux Rootkits Scanner
Rkhunter (Rootkit Hunter) is a free, open-source security monitoring and analyzing tool for POSIX-compliant systems. It runs in the background to inform you of malicious attacks the moment one runs on your machine.
Use it to protect against rootkits, and local exploits, and to hunt backdoors on both servers and desktops.
5. Snort – Linux Network Intrusion
Snort is a prominent open-source Intrusion Prevention System (IPS) for Linux and Windows computers. It features a packet sniffer for real-time traffic analysis which allows for network traffic debugging and IPS. As soon as malicious packets or activity are detected, you will get an alert.
Snort can detect security vulnerabilities thanks to its predefined set of rules against which it scans for malicious network activity. It is definitely a must-have and is available for both personal and business purposes.
6. Wireshark – Linux Packet Analyzer
Wireshark is a free and open-source network protocol analyzer. With it, you can capture and inspect the content of live data packets in real time – a feature that makes Wireshark the only network monitoring tool you will need if you have the right skill set.
It is supported by a global community of network specialists, engineers, and developers who update it with several encryption methodologies and patches.
Wireshark is so feature-rich and trusted by several organizations, and security experts that it is probably the only network traffic inspector you need to develop modern security skills.
7. LMD – Linux Malware Detect
Released under the GNU GPLv2 license, Linux Malware Detect, commonly abbreviated as LMD, is a highly efficient open-source malware scanner that is tailored to detect and extract threats endemic in shared hosted environments.
It leverages a threat database from network edge intrusion detection systems to generate detection signatures which help in efficient malware detection and removal.
The development of LMD was inspired by the limited availability of open-source software tools for Linux environments that focus on accurate malware detection and removal.
Another driving force is that a good number of anti-virus products for Linux environments are inefficient, especially in shared-hosted environments. The threat landscape in shared hosted platforms differs from standard anti-virus products in that threat detection tools are used primarily for detecting OS-level rootkits, trojans, and viruses but fall short in detecting a myriad of malware on the user account level which provides an ideal attack vector for hackers.
8. Suricata – Intrusion Detection System
Suricata is a high-performance and powerful open-source IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) used by users individual users and organizations around the globe to safeguard their systems from external threats.
Suricata uses a set of rules or community-defined signatures to scrutinize or examine network traffic. It scans for suspicious network traffic in a server and generates log alerts which can later be analyzed. You can also configure Suricata to act as an IPS to alert and block network traffic that looks suspicious or matches a specific set of rules in the signature database.
It’s also a perfect logging tool that can log DNS queries, HTTP requests as well as SSL/TLS exchanges. You can deploy suricata on an individual host or as a gateway in a network to scan and examine inbound and outbound traffic from other hosts.
9. Nessus – Vulnerability Scanner
Created by Tenable Inc., Nessus is an open-source but proprietary vulnerability scanner used for penetration testing and vulnerability assessments. It’s a popular tool that is widely used by cybersecurity professionals and system administrators to scan servers and computers for security holes and vulnerabilities that can be exploited by hackers.
During a target scan, Nessus examines each open port on the host to check for any vulnerabilities that might be exploited by hackers. It goes a step further and tests the services running on those ports to see if they are exploitable. It can also detect missing security updates and patches.
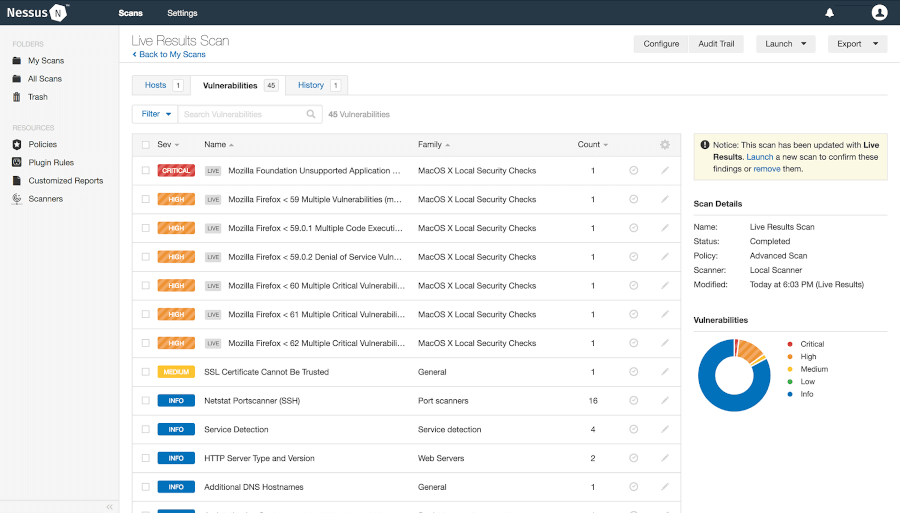
Nessus uses the CVE (Common Vulnerabilities and Exposures) database to reference threats discovered on the target hosts. It uses an assortment of plugins to pick out threats and vulnerabilities. It then displays the severity of the threats based on CVSSv2 scores or CVSSv3 scores. The scan results can be saved and downloaded as PDF reports for later viewing.
10. OpenVAS – Open Vulnerability Assessment Scanner
Developed by Greenbone, OpenVAS is a comprehensive vulnerability scanner that performs vulnerability assessments and scans across various devices. It provides a full-featured scan engine that is continually updated with a list of prevalent vulnerabilities.
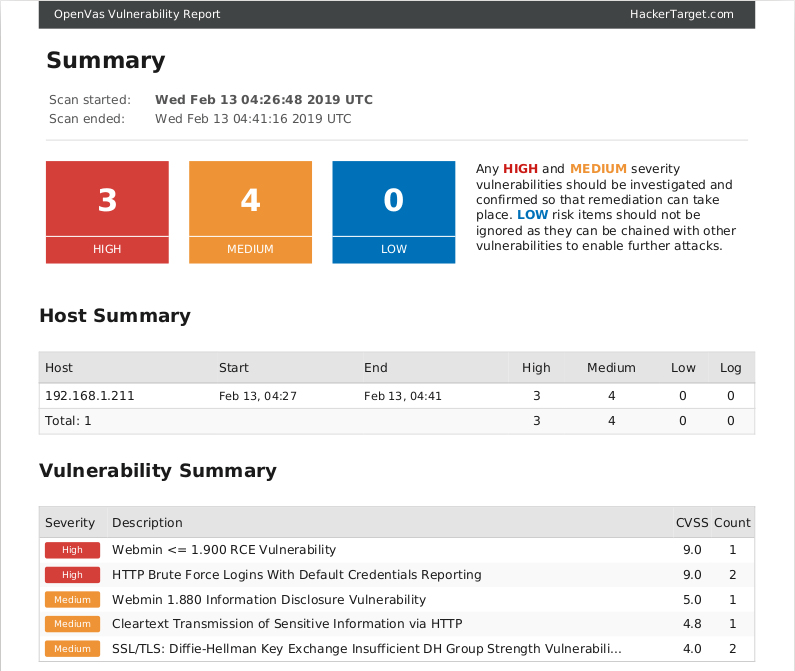
Like Nessus, OpenVAS performs an in-depth analysis of a target’s IP address. This includes a comprehensive port scan to find out open ports and services. It then carries out tests on the services for any vulnerabilities or misconfigurations using an up-to-date database with more than 53,000NVT checks.
Once the scan is complete, the results are compiled into a well-detailed report with information on each vulnerability and any critical issue detected on the target system.
OpenVAS is free and allows you to run vulnerability scans against a wide range of devices including servers and network devices.
11. Lynis – Security Audit Tool
Lynis is an open-source security hardening and auditing tool designed for UNIX-based systems such as Linux, FreeBSD, Solaris macOS, and many others.
Lynis runs penetration tests on target hosts and provides tips for hardening the defenses of your system. During the scans, it probes for information such as vulnerable software packages, misconfigurations as well and general system information.
Apart from system hardening. Lynis also assists with intrusion detection, patch management, and compliance testing (HIPAA, PCI-DSS, and ISO27001).
12. OWASP ZAP – Web Application Security Scanner
OWASP ZAP is a free and open-source web app scanner that is a perfect alternative to Burp Suite. It ranks as one of the world’s most reliable free security tools for detecting security flaws in web applications.
OWASP ZAP performs a myriad of security tasks such as scanning web requests, examining a site’s structure, and retrieving URLs on a page. It can also help you identify misconfigurations and possible threats such as XSS (Cross-site scripting), SQL injection, and exposure of confidential data.
In addition, OWASP ZAP can perform port scans and identify vulnerabilities associated with services running on those ports. You can also intercept and analyze web socket traffic flowing between a server and a client.
OWASP ZAP is actively maintained by a community of vibrant developers.
13. Firejail – Security Sandbox Program
Firejail is a c-based community SUID project that minimizes security breaches by managing the access that applications using Linux namespaces and seccomp-bpf run.
Firejail can easily sandbox servers, GUI apps, and login session processes and because it ships with several security profiles for different Linux programs including Mozilla Firefox, VLC, and transmission, it is simple to set up.
14. John the Ripper – Password Cracker
John the Ripper is among the fastest password crackers and it is available for multiple platforms including OpenVMS, Windows, DOS, and several Unix flavours.
It is open-source and right out of the box it supports Windows LM hashes and its community-enhanced version packs a lot more features like support for more hashes and ciphers.
15. OSQuery – Instrumentation Framework
OSQuery is an open-source and cross-platform framework for analyzing networks and security leaks. It is an industry standard for performing continuous tests to check thread safety and detect memory leaks, and binary reproducibility.
OSQuery enables you to query your devices like you would a relational database using SQL commands for security, compliance, and developer operations.
16. Metasploit – Penetration Testing Software
Metasploit is mainly used for penetration testing but you can also use it for authenticating vulnerabilities, conducting security assessments, and improving your security awareness to stay ahead of potential attackers.
17. Chkrootkit – Rootkit Scanner
Chkrootkit is an open-source utility for detecting local rootkits. A rootkit is any set of software tools used by a 3rd party to hide the changes made to a computer system after a successful security bridge.
18. W3af – Web Application Security Scanner
Written in Python, w3af (Web Application Attack and Audit Framework) is a powerful open-source web application security scanner for performing penetration tests on web applications. It helps developers and security professionals to audit and exploit web applications to identify weaknesses or vulnerabilities.
According to its GitHub page, the w3af framework can identify over 200 vulnerabilities including SQL injection, OS commanding, and Cross-Site Scripting.
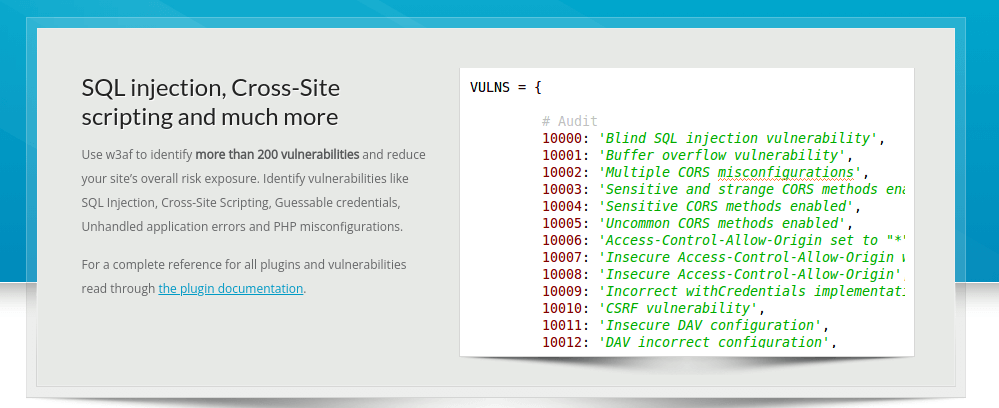
19. Ettercap – Network Security Tool
Ettercap is an open-source tool that is used to simulate man-in-the-middle attacks in a network through ARP poisoning. Depending on how it is used, it can be a network threat used to launch attacks, or a penetration tool to probe for weaknesses.
Network administrators and cybersecurity professionals use Ettercap to find weaknesses in a target system to safeguard it from man-in-the-middle attacks.
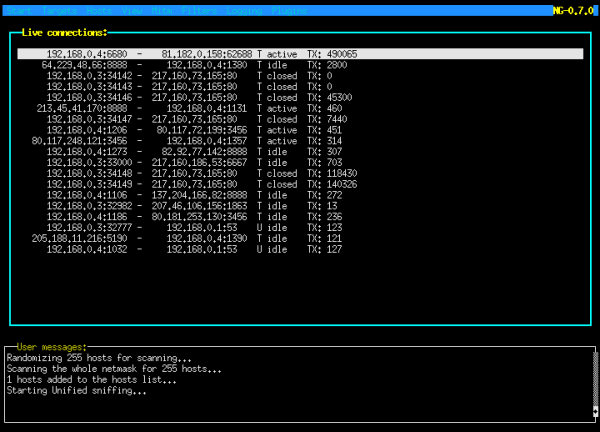
Ettercap provides both a command-line interface and GUI for simulating man-in-the-middle attacks. It can sniff live connections using a powerful sniffing suite, detect a switched LAN, and perform active and passive dissection of multiple protocols to unearth the geometry of a LAN.
20. OSSEC – Host Intrusion Detection System
Written in C language, OSSEC is one of the world’s most popular open-source host-based IDS (Intrusion Detection System). It actively monitors your system for threats and combines log monitoring, host-based intrusion detection (HIDS), and SIEM (Security Information and Event Management ) to detect and alert on threats encountered.
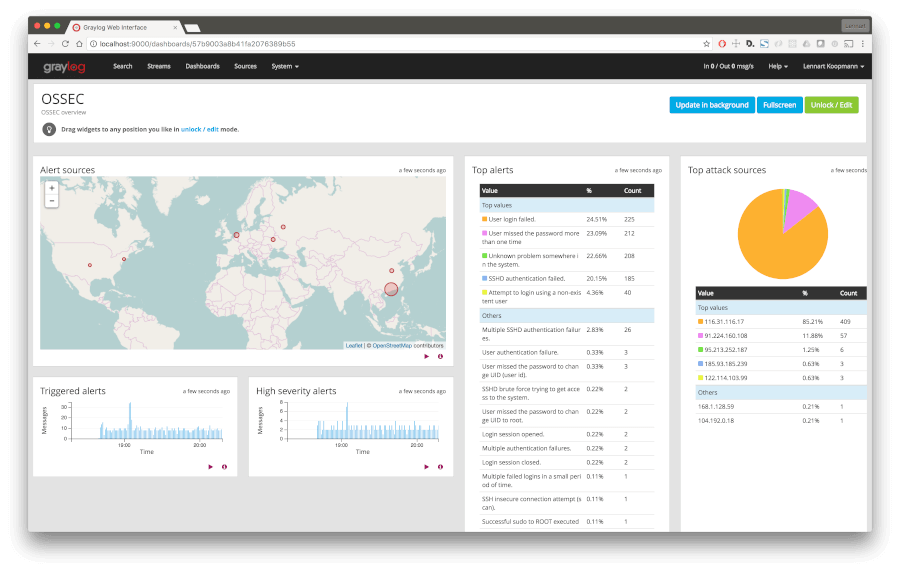
OSSEC can be tailored to meet your security needs through its diverse range of configuration options and custom alert rules which can be tweaked to trigger alerts in case of an event that mimics a security threat.
OSSEC is a great tool in helping organizations stay compliant with compliance agencies such as PCI DSS and NIST.
21. Crowdsec – Collaborative Security Suite
Written in the Go language, Crowdsec is a modern-day Fail2ban, which is a free and collaborative behavior detection engine that safeguards Linux servers including bare-metal, virtual, and cloud servers, as well as containers and services that are exposed to the internet from malicious IPs
Crowdsec uses behavioral analysis to examine the behavior of an external IP that is trying to access your system. It used Grok patterns to parse system logs to identify any unusual activity that might mimic an attack.
Once detected, the offending IP is relayed to CrowdSec for curation and then shared among other users to create awareness. By so doing, everyone stands guard and remains protected. Once detected, threats can be remedied using various ways including blocking them using a firewall, Captchas, etc.
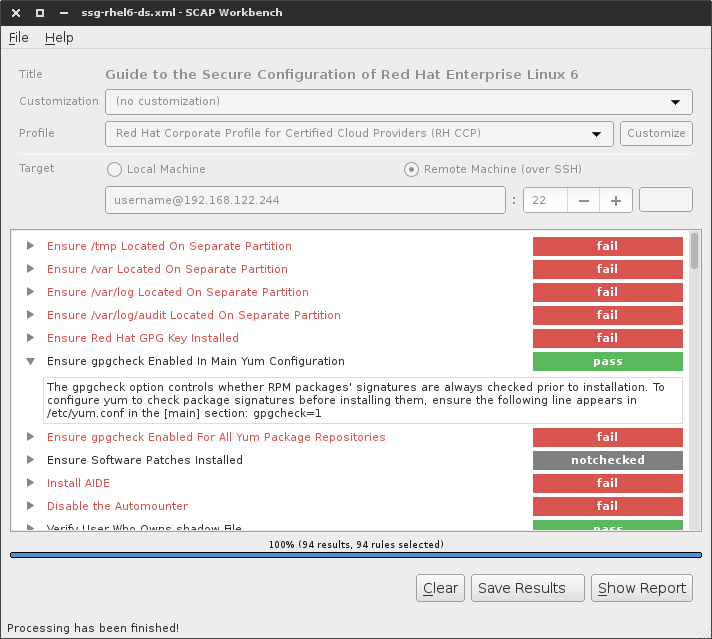
22. OpenSCAP – (Vulnerability and Compliance Scanner)
OpenSCAP offers a suite of versatile tools designed to assist auditors and administrators in evaluating, quantifying, and upholding security standards. It prioritizes flexibility and interoperability, resulting in cost-effective security audits.
With a diverse array of configuration baselines and hardening guides, contributed by the open-source community, you can select the security policy that aligns with your organization’s unique requirements, regardless of its size.
OpenSCAP aligns with the U.S. standard known as Security Content Automation Protocol (SCAP), upheld by the National Institute of Standards and Technology. This open-source project, certified as SCAP 1.2 compliant by NIST in 2014, plays a crucial role in maintaining security compliance within an ever-evolving landscape of emerging vulnerabilities and fixes.
Conclusion
So, there you have it, folks! These are the most important tools that you need to make sure that your network is secure. Technically, they won’t make your network impenetrable but knowing how to use them is one of the first steps towards ensuring security.
Are there any tools that you think should be on this list? You’re welcome to make your suggestions in the comments section below.

I would submit that OpenSCAP should be included in the list.
@Dimitri,
Thank you for your suggestion. OpenSCAP has been added to the article. Your input is greatly appreciated.
Great list but you missed one of the best ones I think! Can you please add CrowdSec?
Open source, crowdsourced protection against malicious IPs.
Why is number 15 (mtr) listed? Does not sound like a security tool.
I created a tool (started in 2007, still maintained) that might help readers. It is Lynis, a security scanner for Linux and Unix systems. Open source and free to use.
Another great article. Your list was spot on, as usual. Having once been a MCSE I tend to keep up with anything related to computer security. Linux, Windows, MacOS, and especially Android. It’s pretty much wired into my subconscious and I always take it seriously.
You did manage to bring a couple of tools to my attention I was not familiar with like Nitco. One thing I have learned through the years is that an ounce of prevention goes a long way. Being aware of the potential threats is the first step in mitigating them. I use many of the tools mentioned, regularly. Usually, the biggest problem I have to deal with is WiFi intrusions. Had to deal with is more accurate because it’s zipped up like Fort Knox now.
Computer security is not something everyone puts a premium on. That always amazes me, too. Just about everyone uses WiFi but does not secure it well. Kali and a laptop, tells me so. The sheer amount of WEP tells me that the owner probably never updates anything or using outdated equipment. Even if that is the case WPA/WPA2 is available, I would think.
Many people are just not security conscious, or savvy. Or, they don’t care. I ran into that all the time when I worked in IT trying to keep Windows workstations secure and working. It was a job. A very stressful job.
I must admit though, that when it came to Windows, the user posed the main problem. Windows has issues, to be sure but the reality is they can be minimized and mostly eliminated with a little effort and know-how. Unfortunately, there is little that can be done when the user practices bad computing habits, such as opening attachments, installing software from shady sources, or dangerous web surfing.
Much of that was prevented in company owned systems thru restriction protocols and other methods. Even with restrictions in place some systems would become infected because of a user visiting a shady site(often porn) that hadn’t made it on the restricted list.
My point, is that the user is either the first line of defense, or the problem. Mostly, it’s the latter. A large part of Windows users practice bad computing habits and believe the fault is the system. Home computers rarely have adequate security implements and are basically ticking time bombs.
Ironically, Linux is the system that type of computer user would be better off using. Those users who are security conscious rarely have many problems, even using Windows. Linux users seem to all be security conscious, by default, and most Windows users that decide to make the switch are cut from the same cloth.
The type of Windows user I was referring to earlier has no interest in security and will not change their habits. They could care less about Linux and will believe something went wrong with Windows when malware takes their system out. The majority will go out and buy a new computer and start the process all over never understanding, or caring, why these things happened.
Those types were a thorn in our side more than Windows ever was. For those of us in IT, it was a running battle and we were always to blame when their system broke. Whenever, we would attempt to educate them they wouldn’t listen and always claimed they did not do anything to cause the problem. They were obviously unaware that everything was logged. Needless to say, I do not miss any of that.
To get back to your article, have you ever tried setting up your own VPN? If so, I would be interested to know the outcome. I have been boning up on the subject and it has me interested. For one, it’s free which is always a bonus (not that I mind paying, especially for peace of mind). Mainly, it’s something I have never attempted and it sounds like it could be a good learning experience. I will let you know my findings and if it was a worthwhile endeavor.
I use NordVPN and have no complaints but my curiosity often dictates my direction.
Such a great list of security tools, I already use Nessus and Wireshark, and I like how they work, I missed nordvpn inside this article, I use it for my privacy as well.
Thank you.
Yes, NordVPN is awesome although it is neither free nor open-source. I mentioned it in a different security and privacy-related post.