Cybersecurity is the process of preventing illegal access, theft, or damage to networks, electronic devices, and sensitive data.
Threats such as online security breaches are occurring at an unprecedented rate, posing a huge threat to sensitive and highly confidential information such as financial records, usernames, and passwords.
Access to this data by a cybercriminal invariably leads to serious problems such as the sharing of private information, the selling of data to unaffiliated parties, the alteration of data to fit their purposes, the use of data for financial theft, and more.
A survey shows that cybersecurity threats are growing frequently and at a sophisticated rate. Phishing attacks surged by 48% in the first half of 2022, with reports of 11,395 occurrences costing organizations $12.3 million.
One method to achieve optimal security is to keep an eye out for weaknesses in the IT environment and take action before hackers take advantage of them.
Encrypting network communications, safeguarding systems against assaults carried out through endpoints, and preventing unauthorized access to networks are all aspects of Cybersecurity.
In today’s guide, we showcase the best cybersecurity tools for protecting networks, devices, and data from unauthorized access, theft, and damage.
1. Snort – Network Intrusion Detection System
Snort is an open-source tool that examines network traffic in real-time and keeps an eye on each packet to spot potential vulnerabilities.
Library packet capture (Libpcap) is the foundation of Snort. Content matching, packet logging analysis, real-time web analysis, network traffic surveillance, and protocol analysis are just a few tasks Snort can accomplish.
As soon as a threat is identified, the application alerts organizations to the need for preventative action. In addition, there are no licensing fees or software maintenance upgrades needed for this cyber security assessment tool, and it also handles network packet tracking and data streaming to the screen assignments.
With Snort, enterprises can identify potentially harmful threats on their networks and take preventative action to stop attacks before they start.

2. Wireshark – Network Packet Analyzer
Wireshark is one of the cybersecurity forensic tools used to monitor and analyze network protocols. It helps professionals identify and examine possible security risks and susceptibilities in computer networks.
Wireshark offers useful insights into unauthorized access attempts, malicious code, and suspicious activity by collecting and examining data packets as they move through the network.
It provides an intuitive interface that lets users see, filter, and understand data. It is a useful tool for network administrators and cybersecurity specialists to ensure the security and stability of their systems.
Since Wireshark is a free network sniffing program, there is no fee associated with using it. The cybersecurity program supports a variety of operating systems, including Windows, Mac, Linux, FreeBSD, Solaris, and others.
Additionally, Wireshark provides offline analysis and live capture. Some of the technical information in Wireshark includes:
- Capable of exporting output to CSV, XML, or legible text
- Offers a comprehensive VoIP analysis
- ISAKMP, WPA/WPA2, WEP, IPsec, and SSL/TLS are just a few of the protocols that Wireshark can decrypt.
- Reads information from Bluetooth, PPP/HDLC, USB, Token Ring, ATMs, and the internet, among other sources.
- It features the standard three-pane packet browser
3. Nmap – Network Security Scanner
Nmap is a free and open-source cybersecurity application that scans networks and IT systems for weaknesses or security flaws. In addition, it is used for other crucial tasks like service or host uptime monitoring and network attack surface mapping.
Besides that, it is beneficial for scanning hosts on big and small networks for web vulnerabilities and works on the majority of popular OS systems.
The hosts connected to the networks, the kinds of firewalls or packet filters used to secure a network, and the operating system in use are some of the features that this tool packs.
Nmap offers the following advantages, which include:
- Ability to Create graphical network maps for improved reporting and usability.
- You can use Nmap to attack systems with pre-existing scripts from the Nmap Scripting Engine during security audits and vulnerability scans.
- Capability to identify every device on single or multiple networks quickly, including servers, switches, routers, mobile devices, etc.
- Detailed information, such as OS versions, can be obtained using Nmap, which facilitates the planning of additional penetration testing strategies.
4. Ncat – Networking Utility
Ncat is a feature-rich networking tool that can be used from the command line to read and write data across networks. Ncat was developed as a much-enhanced version of the old Netcat for the Nmap Project. This tool is tailored to be a dependable back-end utility that rapidly connects users and other programs to the network.
In addition, It communicates with users using both TCP and UDP and packs features such as support for SSL, IPv6, SOCKS, and HTTP. File transmission, port scanning, and network debugging are just a few of its uses. Besides that, Ncat can be used as a backdoor to access a victim’s computer.
Because of its adaptability and practicality in a variety of situations, cybersecurity experts highly value this tool. Along with Nmap, Ncat can be downloaded as part of the regular Nmap distribution packages from the Nmap download page. These packages include source code as well as Linux, Windows, and Mac binaries.
5. John the Ripper – Password Cracker
For good reason, a lot of security enthusiasts love John the Ripper, a system that was initially created for the UNIX operating system. It has subsequently developed into a tool for identifying weak passwords that could compromise a system and is compatible with a variety of other operating systems, including Windows, DOS, OpenVMS systems, and more.
This tool packs advanced features, such as providing a variety of modes for quick password cracking and software that assists in recovering passwords. It also works across 19 distinct platforms.
John the Ripper uses the rainbow table technique to crack passwords, which is used in the majority of cyberattacks. This software takes a sample from a list of words that are commonly found in dictionaries and compares the hashed password to the password in the file that is being matched.
When performing penetration testing activities, the password cracker is mostly utilized. IT specialists utilize this program to identify weak passwords and bad password practices.
6. Nikto – Vulnerability Scanner
One tool for finding vulnerabilities in web servers is Nikto, an open-source, free web server scanner. It can check for issues including out-of-date server software, hazardous files, and other issues. It can carry out both general and server-type specific checks.
You can use this command-line utility to record and print any cookies you receive. It also verifies that the web server software is installed, that numerous index files are there, and that HTTP server configurations exist.
Nikto is the ideal software for general web server security assessments. You can scan multiple web servers fast. The downside to this is that these scans can easily be picked up as intrusions by intrusion detection systems. To carry out covert scans, take advantage of the anti-IDS plugin support.
7. Burp Suite – Software Security Testing
Burpsuite includes all the solutions you need for pen-testing web applications. It is designed to be a one-stop shop for all things web application pen-testing.
Burpsuite’s suite of tools supports the entire web application testing lifecycle. Besides that, it provides all the tools required to breach online applications, from scanning to exploitation.
The capability of Burp Suite to intercept HTTP requests is one of its primary features. Typically, a web server receives HTTP requests from your browser and responds to them. You can alter the request and answer by using man-in-the-middle techniques using Burp Suite.
Burpusite’s user interface is intuitive and offers automation solutions to help you work more quickly and effectively.
8. Metasploit – Penetration Testing Software
It’s evident from reading any Metasploit review that Metasploit is an excellent set of security tools that work well for penetration testing. Security professionals use this open-source tool to accomplish various cybersecurity goals, including identifying network and system vulnerabilities, creating strategies to strengthen an organization’s security defenses, and so much more.
From a penetration testing perspective, Metasploit can be used for a variety of tasks, such as threat scanning, listening, and exploiting threats that are found. This tool can also be used for evidence collection and project reporting.
Technical information regarding the use of Metasploit includes:
- Features a command-line interface and GUI
- Vulnerability scanner import
- Network discovery
- Module browser
- Compatible with Windows, Mac OS X, and Linux
- The software’s Community Edition is available for free use by the Infosec community.
H.D. Moore, a cyber security expert, hacker, and programmer, created Metasploit, which is among the best tools for cybersecurity.
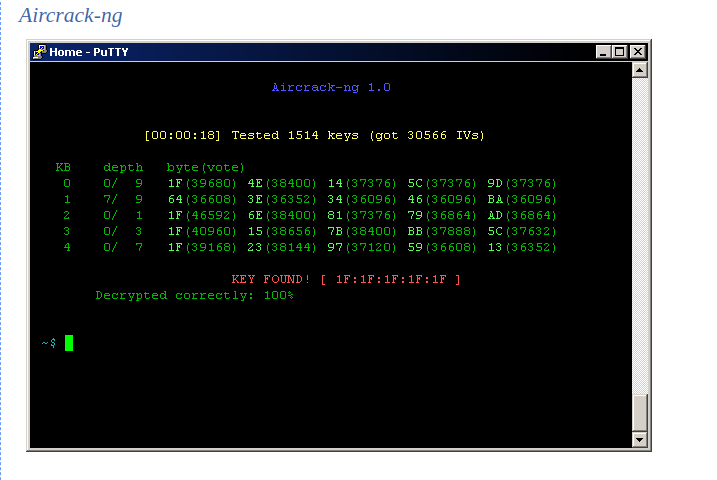
9. Aircrack-ng – WiFI Password Cracker
A whole toolkit for evaluating WiFi network security is available with Aircrack-ng that provides functions such as testing, monitoring, attacking, cracking, and more.
Aircrack-ng can capture and export packet data to text files for further processing with other applications. Sophisticated algorithms are included in Aircrack to crack WiFi passwords and record wireless data. Additionally, it is capable of decrypting encrypted packets, completing the set of tools for wireless penetration testing.
To put it briefly, Aircrack may be used to spy on, target, and troubleshoot any kind of wireless network.
10. Nessus – Vulnerability Scanner
Nessus is a remote security scanning tool that scans a computer and sounds an alarm if it finds any security flaws that could allow malevolent hackers to access any computer that is connected to the network.
To achieve this, it runs over 1200 checks on a specific computer to see if any of these attacks have the potential to compromise it or harm it in some other way. Tenable, Inc. develops this startup, and it is offered in both free and paid versions.
Nmap can be used to scan and locate ports or services, but Nessus will provide you with a list of vulnerabilities and details on how to exploit them. Tens of thousands of plugins, an outstanding user interface, and embedded scripting support are all features of Nessus.
Businesses often tend to pick this tool because it facilitates audits for a variety of compliances, including PCI and HIPPA.
Conclusion
Cybersecurity tools are crucial because they guard against theft and damage to information of all kinds. This data may consist of personally identifiable information (PII), protected health information (PHI), and government corporate information systems. No matter where they are used, these tools guarantee cybersecurity.

You need a very good level of computer science to understand these software. For poor average users like me have no choice but to put a rabbit’s foot on their PC and pray.
@Legrand,
Remember, everyone starts somewhere, and with a bit of patience and persistence, you can become more proficient in using software without relying on luck.
Using software like DeepFreeze or Shadow Defender can help keep your computer clean. You can do your banking activities, and then simply reboot your computer to prevent malware from entering.